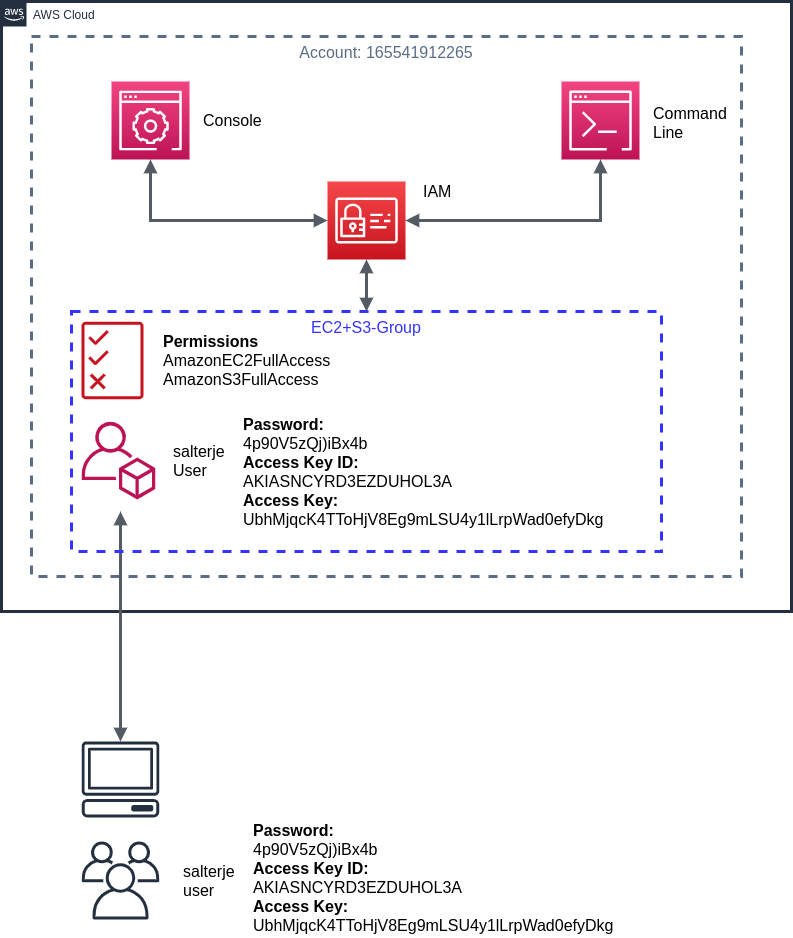
In this Lab we will create a new AWS user that will have access to an existing AWS account (165541912265) to create EC2 Virtual Machines and S3 Object Storage.
This involves setting up a new user with the IAM service and giving it the appropriate permissions. To do this we will actually create a new group with full permissions for EC2 and S3 and nothing else.
The new user can then be added to this group to inherit these permissions (by default newly created users don't have any permissions).
For obvious reasons the user will be deleted after the Lab.
Creation of EC2+S3 Full Access Group
We will add a new group to our AWS account giving full access to EC2 and S3 (to keep things fairly simple). This group will be used when we create the new user (as we will add the user to it).
This makes it easy to add further users with the same permissions, or to remove the user from the group to remove the permissions.
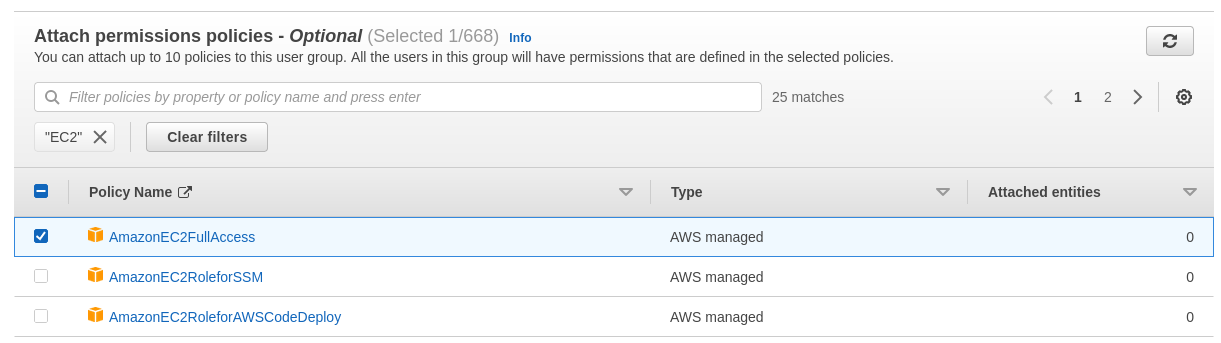
We will then add the EC2 and S3 Full Permissions to the group, in this case there are already some AWS managed policies that can be added by simply searching and ticking the desired policies.
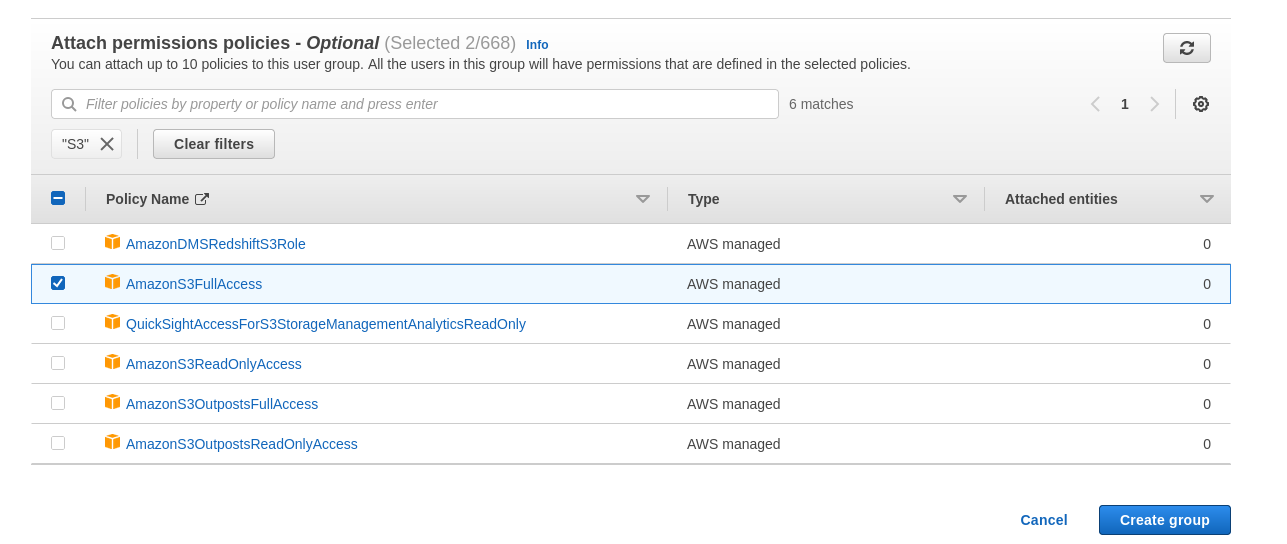
Once this is done we have created our group with appropriate policies and it just remains to create a new user and add them to the group.
Creation of New User and Addition to the Group
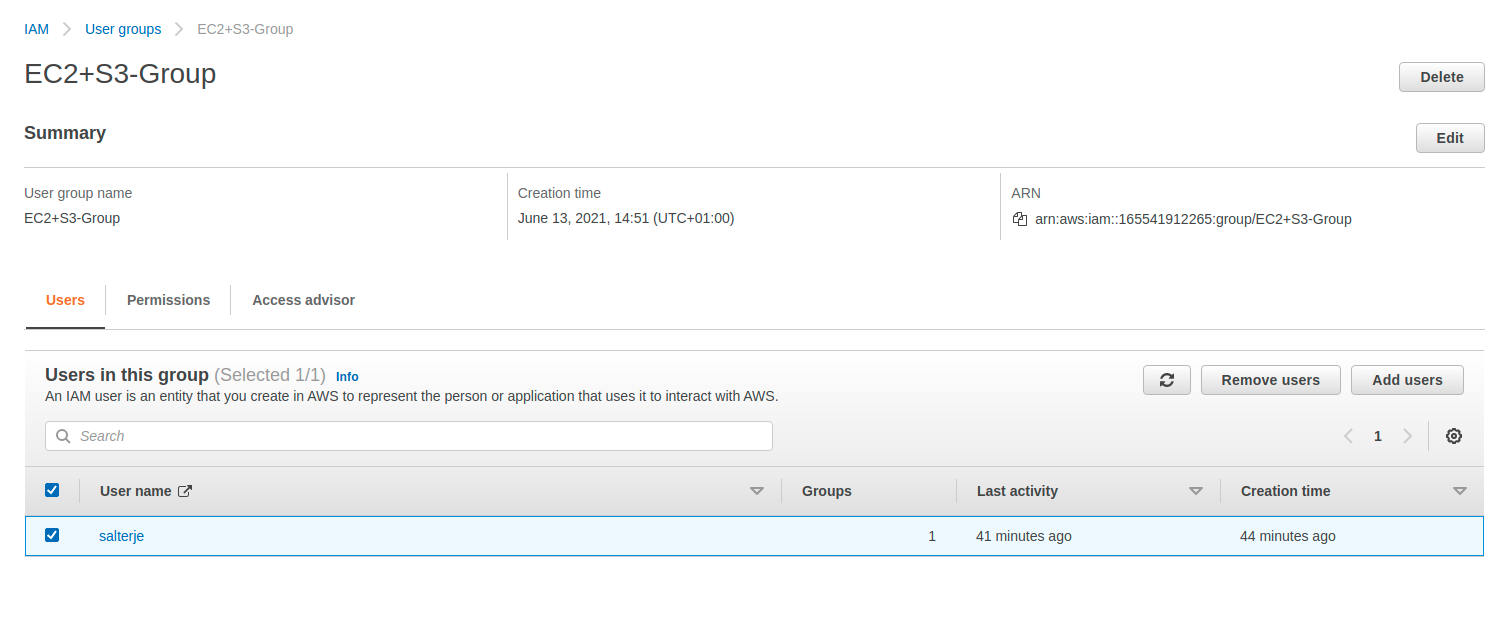
We will now create a new user, salterje, that will be added to EC2+S3-Group. This will allow this user to inherit the appropriate permissions that we need to create EC2 and S3 instances.
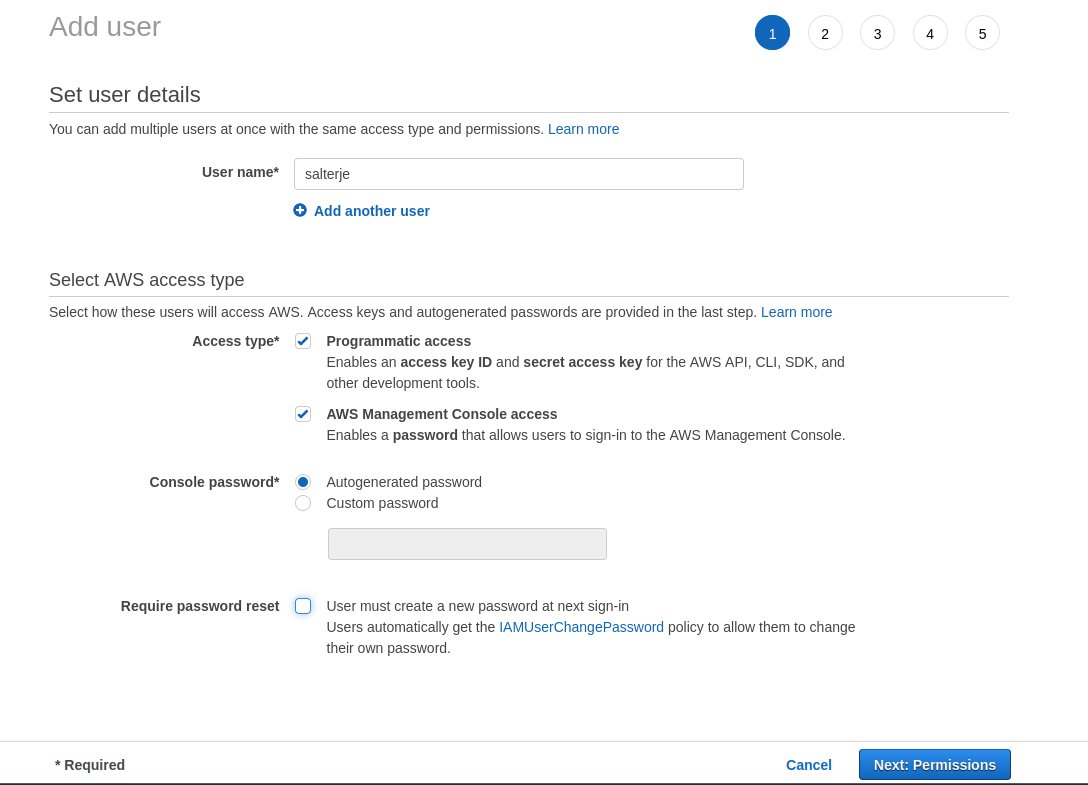
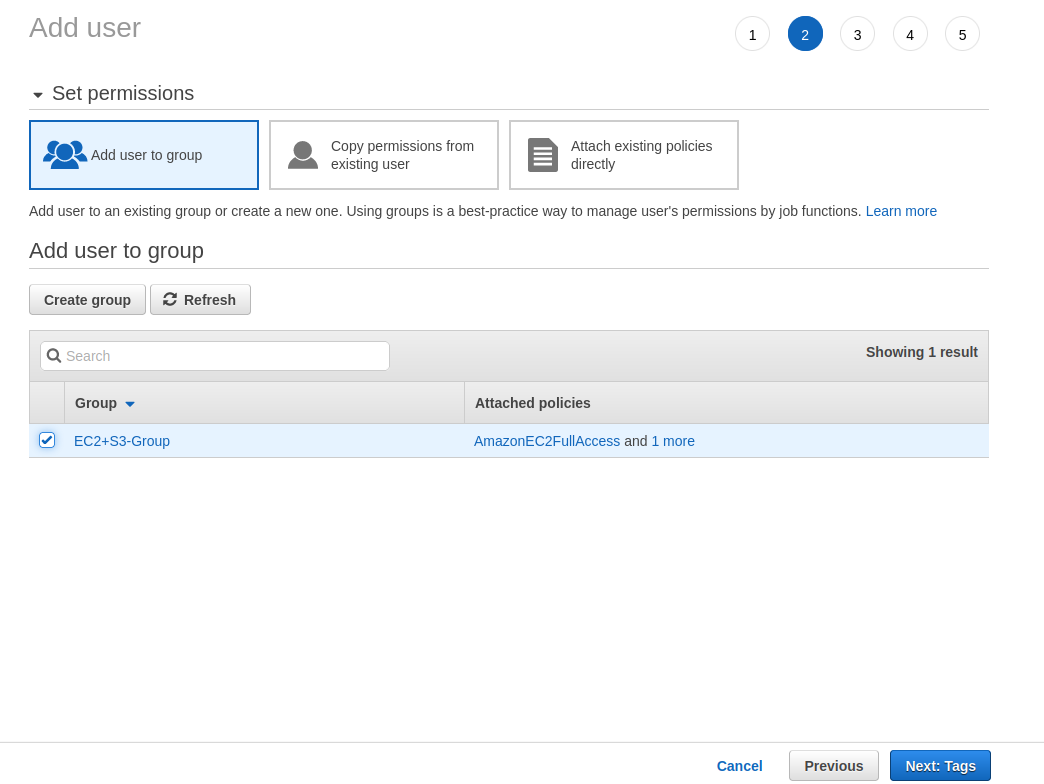
This will create a new user that has access to the AWS console as well as suitable access keys to allow use of the AWS commandline and SDK (although for the purposes of this lab we will just use the console to test).
We will be prompted to download these details to allow us to login to our account as the newly created salterje user.
Testing of the New User
We will login to the account with the downloaded credentials.
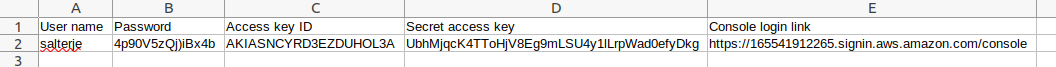
All the necessary details can be found in the .csv file that is available at the last step of user creation. It is important that these credentials are looked after carefully as they contain everything that is needed to access the account as the newly created user.
We will log into the account console with our new user, making use of the URL that was included in the user details.
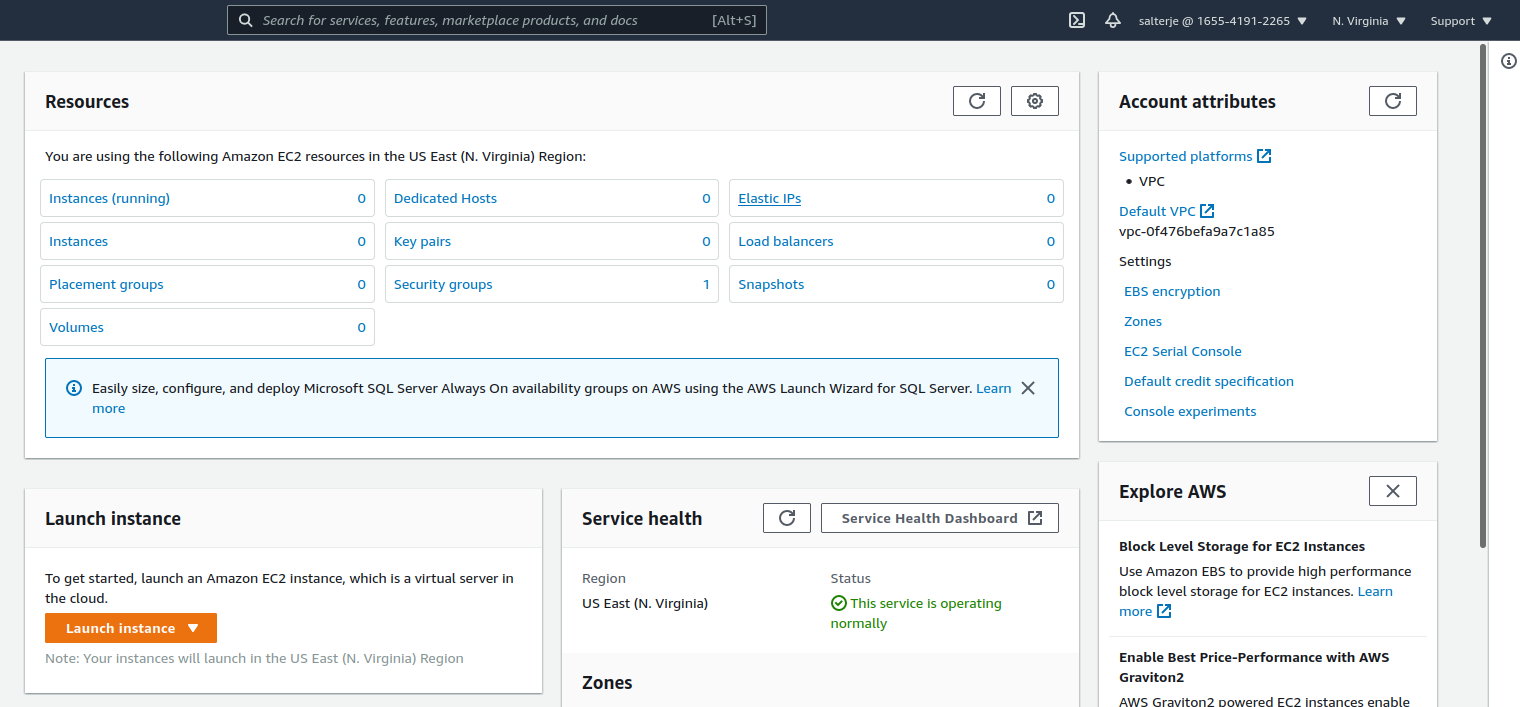
It can be seen at the top right hand corner of the console that we are logged in as salterje
We can now create and view a new EC2 instance and a new S3 Bucket.
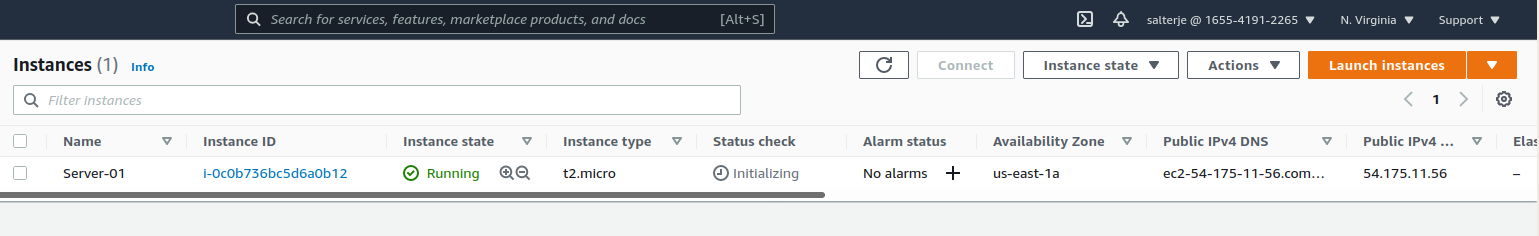
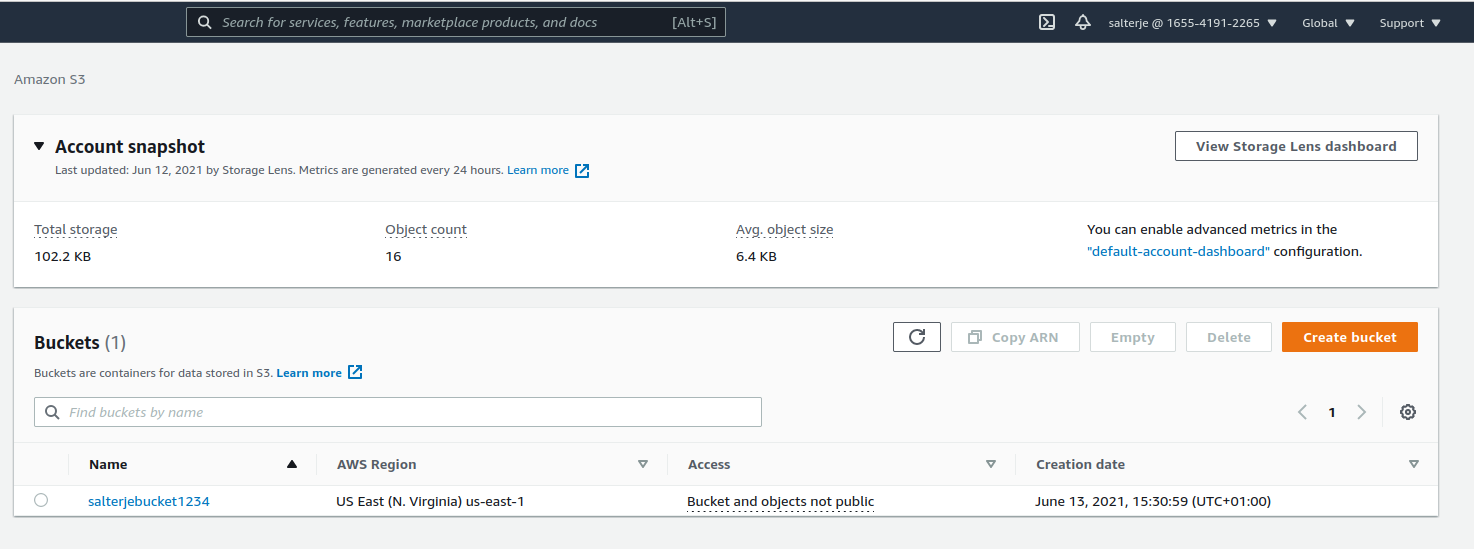
This proves that the user has the appropriate permissions to create these resources but to prove that we don't have access to all resources we will now try to create an RDS Database.
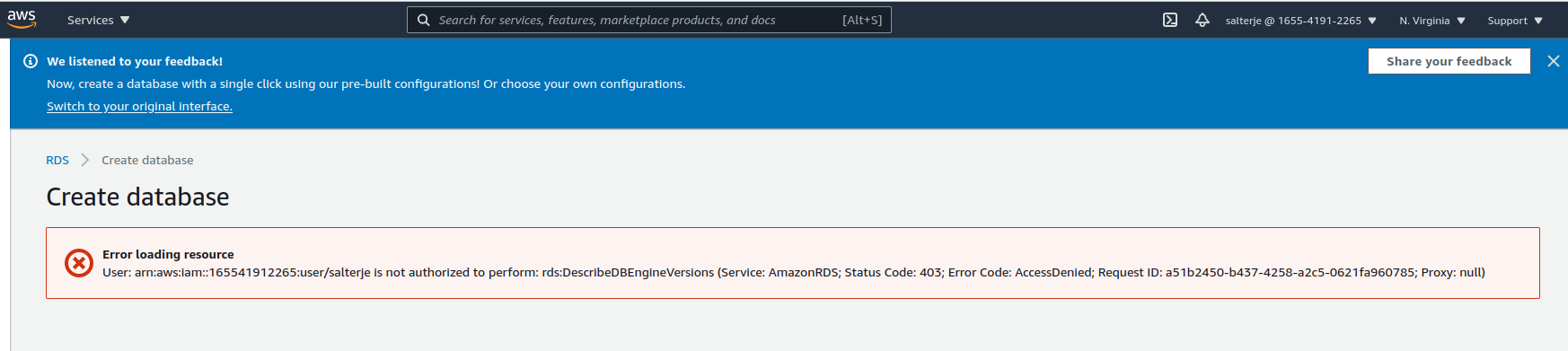
We can see that we don't have the appropriate permissions to create the Database.
Removal of User From Group
Our last test with the salterje user permissions is to remove the user from the EC2+S3-Group. This must be done from our original user that has the appropriate permissions to remove users from their IAM groups.
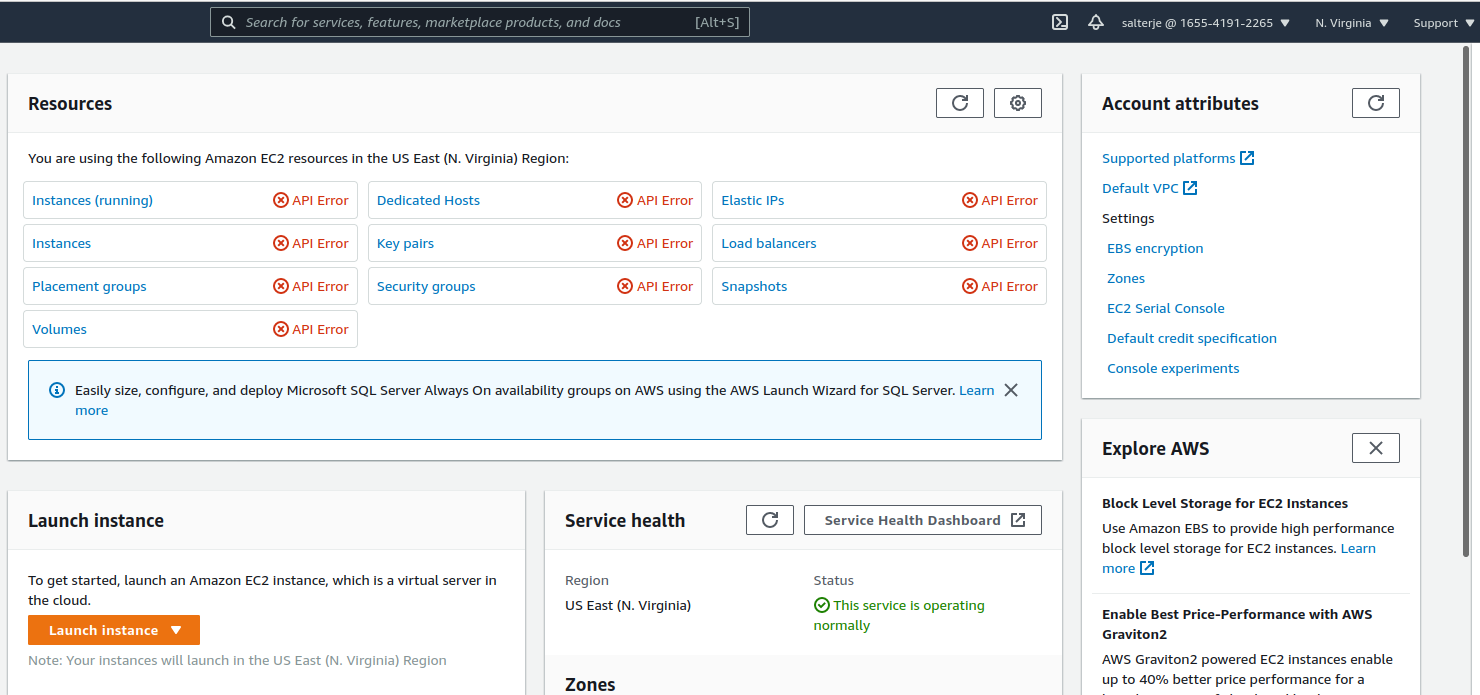
Once this is done it can be seen that the salterje user can no longer even view EC2 or S3 instances, let alone perform any action. This happens as soon as the user is removed from the group.
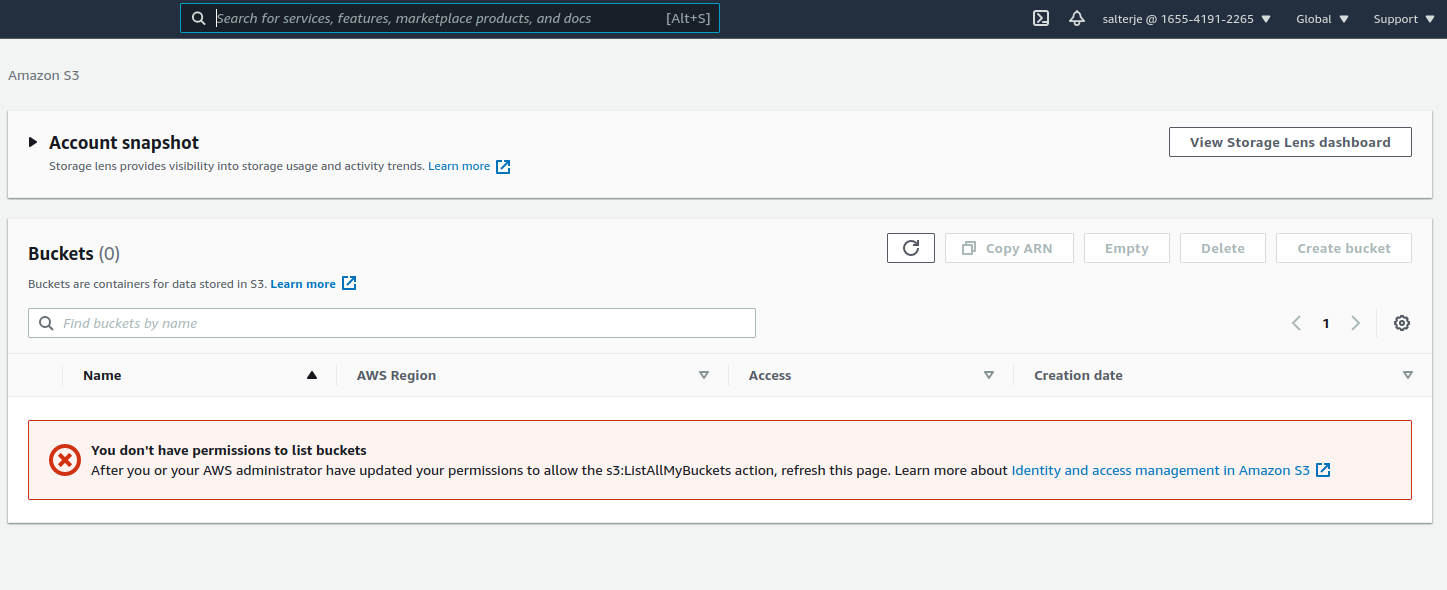
As we have made use of the group to generate the permissions it is easy to add or remove users (for example when people join or leave an organization).
Conclusions
This Lab shows the concept of user and group policies within AWS. In this case we have added a new user to a group that allows the creation of EC2 and S3 resources but nothing else.
We also saw that it is a simple case of removing the user from the group and once this is done they no longer have any access to their resources.
When a user is created all details can be downloaded which will allow the newly created user to log in using the appropritate account URL and password.